Security firms McAfee Labs and Symantec have issued warnings that a type of bitcoin-demanding ransomware, CTB-Locker, is now being propagated through spam campaigns.
The malware, the name of which stands for 'Curve Tor Bitcoin Locker', was first identified last year. However, the spam distribution approach appears to be a relatively new development.
McAfee published its latest advisory last week, describing CTB-Locker as a form of ransomware that encrypts files on the target computer. Anecdotal evidence suggests .jpg image files are a frequent target. The victim then has to pay a ransom to have the files decrypted.
that the process of dealing with crypto malware is “particularly nasty to deal with”.
How it works
Upon installation, CTB-Locker injects malicious code into the 'svchost.exe' file, creating a scheduled task for moving and encrypting files.
The malware encrypts the compromised files using elliptical curve encryption, which appears to be equivalent to RSA encryption with a 3,072-bit key.
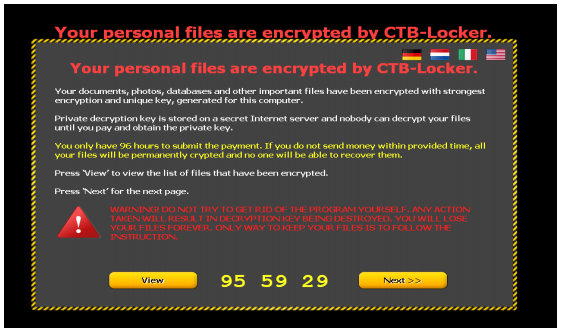
Once the encryption is complete, the user is informed of the attack through a pop-up ransom message.
The message displays a 96-hour countdown. If the user does not pay the bitcoin ransom within 96 hours, the decryption key is destroyed and the files remain permanently encrypted.
screenshot-kc.mcafee.com 2015-01-26 12-34-48
The pop-up allows the user to see the list of encrypted files, along with information on how to make a payment and get the decryption code.
Detection, infection and propagation vectors
McAfee detects CTB-Locker under three different names: BackDoor-FCKQ, Downloader-FAMV and Injector-FMZ. Symantec identifies the final payload as Trojan.Cryptolocker.E.
The malware is being propagated via spam campaigns, as a .zip archive stored within another .zip file. The zipped file contains the downloader for CTB-Locker.
So far, researchers have uncovered the following names used to store the downloader:
- malformed.zip
- plenitude.zip
- inquires.zip
- simoniac.zip
- faltboat.zip
- incurably.zip
- payloads.zip
- dessiatine.zip
Aside from standard sound security practices (eg: not opening .zip files from untrusted sources), McAfee has published a number of recommendations to mitigate the threat using McAfee products.
The Symantec blog also offers useful information on CTB-Locker for users of Symantec security products.
Should victims be unwilling or unable to pay the ransom, there is virtually no way of recovering the encrypted files. The best way of reducing the impact of a potential crypto ransomware attack is to backup valuable files on a regular basis.
CTB-Locker pop-up image via Symantec; Spam image via Shutterstock.
DISCLOSURE
Please note that our privacy policy, terms of use, cookies, and do not sell my personal information has been updated.
The leader in news and information on cryptocurrency, digital assets and the future of money, CoinDesk is a media outlet that strives for the highest journalistic standards and abides by a strict set of editorial policies. CoinDesk is an independent operating subsidiary of Digital Currency Group, which invests in cryptocurrencies and blockchain startups. As part of their compensation, certain CoinDesk employees, including editorial employees, may receive exposure to DCG equity in the form of stock appreciation rights, which vest over a multi-year period. CoinDesk journalists are not allowed to purchase stock outright in DCG.
:format(jpg)/cloudfront-us-east-1.images.arcpublishing.com/coindesk/D2BNO2CSTFHAFF3EQW5DHOBDMI.jpg)

:format(jpg)/cloudfront-us-east-1.images.arcpublishing.com/coindesk/HDGHIKVTEFDLJO55K3VPFLJHHI.jpg)
:format(jpg)/cloudfront-us-east-1.images.arcpublishing.com/coindesk/BKU7YUGJABFMTCDUTEWQUX6JPY.png)
:format(jpg)/cloudfront-us-east-1.images.arcpublishing.com/coindesk/FRTEHPXRCVC3LGJ2LOLOBVB7RA.jpg)
:format(jpg)/cloudfront-us-east-1.images.arcpublishing.com/coindesk/HFTBVAT3OFFFPFYB66C47WRVEI.jpg)