A cybersecurity firm has warned cryptocurrency users to expect more attacks from North Korea as its hackers develop "enhanced capabilities" to deliver malware through popular messaging app Telegram.
Moscow-based Kaspersky Labs has been analyzing new attacks from the Lazarus Group, a cybercrime group with links to North Korea, to determine how its techniques have developed since the AppleJesus attack on several cryptocurrency exchanges in 2018.
In research published Wednessday, the cybersecurity firm said there have been "significant changes to the group's attack methodology."
One case study involved what appeared to be a software update for a fake cryptocurrency wallet that, once downloaded, began to transmit user data to hackers. Another example involved creating a backdoor for Mac software that bypassed security mechanisms without the computer ever being aware it was under attack.
A seemingly new attack vector has been to deliver malware via files distributed on the Telegram messaging app. Researchers found computers downloaded manipulated software, which originated from the group's website, with embedded malware that would send sensitive data to hackers without the victim even being aware.
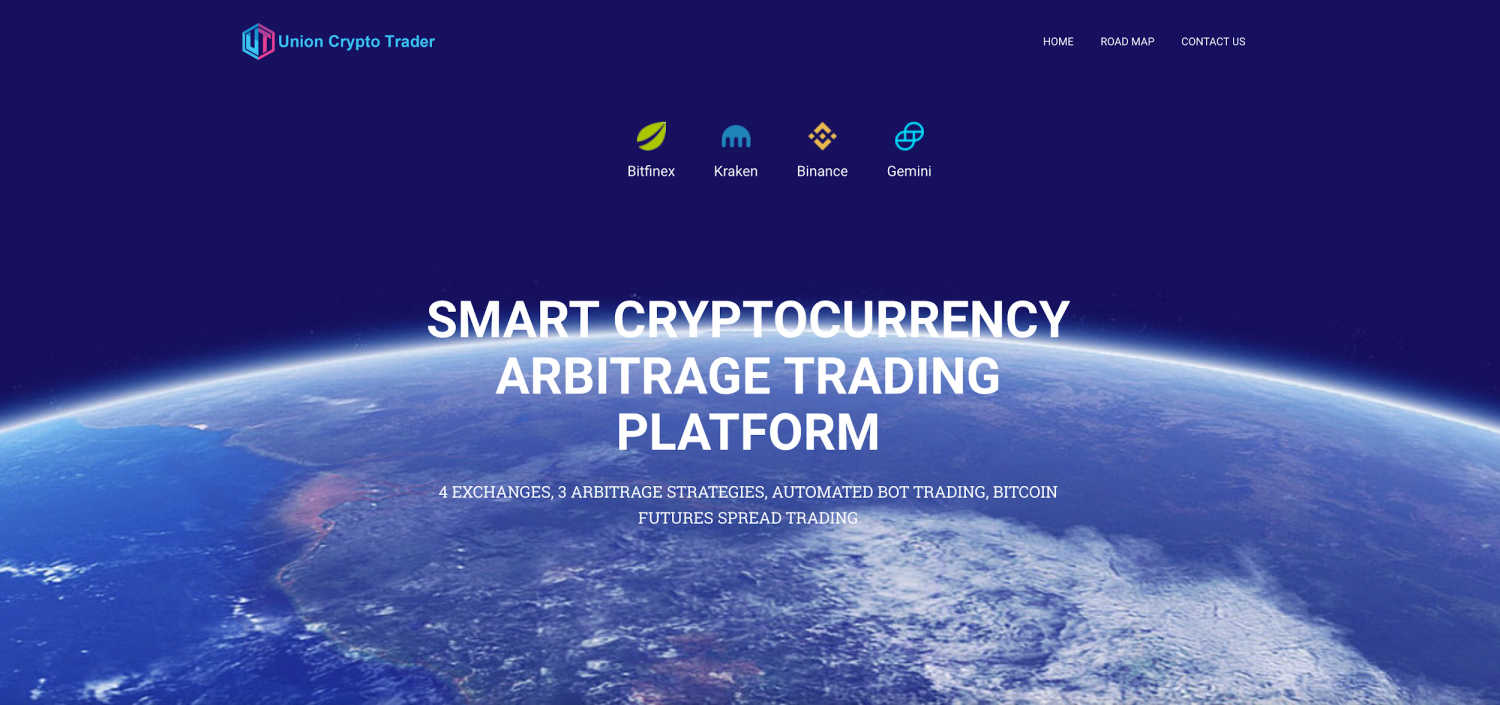
Many of these channels were for fake cryptocurrency companies, presumably set up by the hackers themselves. One recently detected fake site was for a "smart cryptocurrency arbitrage trading platform." Kaspersky researchers found these websites were often incomplete and filled with broken links, aside from the ones that took visitors to the Telegram channel.
Kaspersky said it was able to identify "several victims" from Poland, Russia, China and the U.K., most with links to cryptocurrency businesses.
But Lazarus itself remains a mystery. By running malware through computer memory rather than a hard disk drive, the group generally avoids detection. Although the group is widely believed to be affiliated with North Korea, the secretive regime has repeatedly denied responsibility for its attacks.
Cybersecurity firm Group-IB estimated the group stole nearly $600 million worth of cryptocurrency in 2017 and most of 2018. Because its attacks are so successful, Kaspersky researchers are convinced the group will continue stealing cryptocurrency. "This kind of attack on cryptocurrency businesses will continue and become more sophisticated," the report reads.
The U.S. Department for Treasury placed the Lazarus group on the U.S. sanctions list in 2019, meaning that any financial institution found dealing with it faces sanctions. This week, ethereum developer Virgil Griffith was indicted by U.S. authorities for speaking at a conference in North Korea. If found guilty, he faces up to 20 years in prison.
DISCLOSURE
Please note that our privacy policy, terms of use, cookies, and do not sell my personal information has been updated.
The leader in news and information on cryptocurrency, digital assets and the future of money, CoinDesk is a media outlet that strives for the highest journalistic standards and abides by a strict set of editorial policies. CoinDesk is an independent operating subsidiary of Digital Currency Group, which invests in cryptocurrencies and blockchain startups. As part of their compensation, certain CoinDesk employees, including editorial employees, may receive exposure to DCG equity in the form of stock appreciation rights, which vest over a multi-year period. CoinDesk journalists are not allowed to purchase stock outright in DCG.
:format(jpg)/cloudfront-us-east-1.images.arcpublishing.com/coindesk/P5CGTEYBT5FPLAMSKN4R63YITU.jpg)

:format(jpg)/cloudfront-us-east-1.images.arcpublishing.com/coindesk/VY6PMML5NJGU5GR2EWMUDCXE44.jpg)
:format(jpg)/cloudfront-us-east-1.images.arcpublishing.com/coindesk/KVUYUXDYTZANDALMUFGZ3ME2GU.jpg)
:format(jpg)/cloudfront-us-east-1.images.arcpublishing.com/coindesk/JRTYX3R5WFCZRAL2J7DFGPP3UA.jpg)
:format(jpg)/cloudfront-us-east-1.images.arcpublishing.com/coindesk/PN2SE2FZFVG3ZPSQW2KBZYRG6Y.jpg)