An advanced form of cryptocurrency-targeting malware shared through pirated software and games downloaded from torrent sites poses multiple threats to victims.
- In a report Wednesday, researchers at Slovakian cybersecurity firm ESET said they had found malicious code within the installer program for media files that contains a cryptocurrency mining bot.
- However, the malware has evolved in its two years of existence to possess other tricks that are more concerning to users of cryptocurrency.
- Dubbed "KryptoCibule" – a combination of the Czech and Slovak words for "cryptocurrency" and "onion" – the malware can also change a wallet address to one linked to the hacker when pasted from the clipboard, potentially diverting funds sent to the victim.
- Further, it will hunt for, and steal, cryptocurrency passwords, private keys or key phrases stored on the host machine's hard drive.
- The malware is spread by users sharing the affected media files on peer-to-peer file-sharing networks.
- It also updates itself using BitTorrent, which was acquired by Tron in mid-2018, the researchers said.
- ESET said KryptoCibule had stolen roughly $1,800 in bitcoin and ether by changing victims' wallet addresses.
- They were unable to determine how much the hacker stole through the mining bot or from stealing passwords.
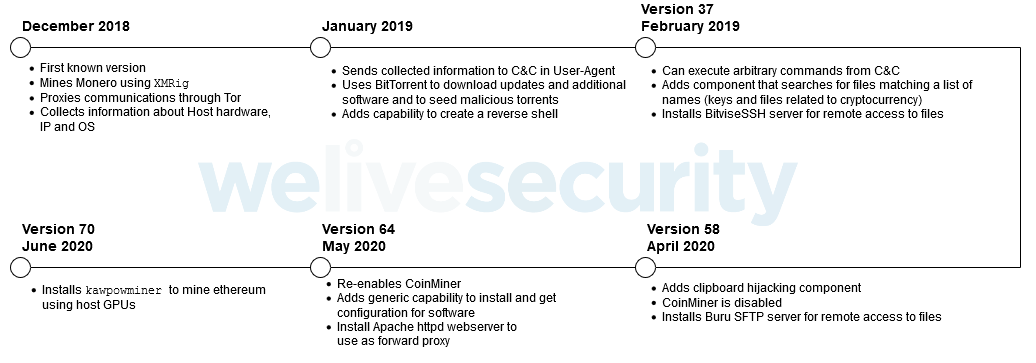
KryptoCibule evolution
- KryptoCibule likely started operation in late 2018 but has remained hidden till now thanks to being designed to evade detection.
- KryptoCibules hides in files that work normally, so victims are less likely to suspect anything amiss. It also actively watches for, and hides from, antivirus tools such as Avast.
- In addition, it contains a command line to the Tor browser that encrypts communications and makes it impossible to trace the mining server behind KryptoCibule.
- KryptoCibule also monitors the computer's battery so it doesn't consume too much power and thus get noticed.
- If the battery falls below 30%, KryptoCibule shuts off the GPU miner and runs its monero miner at a much lower capacity. The whole program shuts down should battery go under 10%.
- Despite its sophistication, ESET said the bot had so far only been downloaded by several hundred computers, mostly based in Czechia and Slovakia.
DISCLOSURE
Please note that our privacy policy, terms of use, cookies, and do not sell my personal information has been updated.
The leader in news and information on cryptocurrency, digital assets and the future of money, CoinDesk is a media outlet that strives for the highest journalistic standards and abides by a strict set of editorial policies. CoinDesk is an independent operating subsidiary of Digital Currency Group, which invests in cryptocurrencies and blockchain startups. As part of their compensation, certain CoinDesk employees, including editorial employees, may receive exposure to DCG equity in the form of stock appreciation rights, which vest over a multi-year period. CoinDesk journalists are not allowed to purchase stock outright in DCG.
:format(jpg)/cloudfront-us-east-1.images.arcpublishing.com/coindesk/IBVOQI7HKVDC5JYKT724ILMXSQ.jpg)

:format(jpg)/cloudfront-us-east-1.images.arcpublishing.com/coindesk/PFEHNV7HU5CCPFROJKQIPWNYJU.jpg)
:format(jpg)/cloudfront-us-east-1.images.arcpublishing.com/coindesk/YLVK7NL7PJAVRJVREC7DTR6XME.jpg)
:format(jpg)/cloudfront-us-east-1.images.arcpublishing.com/coindesk/EXPOIBREMFHSHA7CVOGJ5TDWUY.jpg)
:format(jpg)/cloudfront-us-east-1.images.arcpublishing.com/coindesk/PJTR3KRDWJCRVE3QREM6KUOK7A.png)